
IOUs on the XRPL is a fantastic feature. It allows anyone to issue tokens, and anyone who trusts that the tokens are valid can add a trustline to be able to trade, send, and receive the token.
It also has its downsides, as there is no protection of token names (except for “XRP”), everybody can issue a USD, EUR, or BTC token. Still, there are no guarantees that the token represents any value at all.
This makes any analysis into value transferred on the XRPL, except for that of XRP, worthless. E.g., looking at raw numbers from the XRPL on December 12, 2019, more than 30,000,000 BTC was sent in 116,000 payments. But it is highly unlikely that the tokens were actually representing any value.
The numbers used in this article are from early January 2020.
Diving into IOUs
The key element of the IOU feature is trustlines (or more technically correct, “RippleStates”) – which is an object shared by two accounts to keep track of the balance, the issuer, and the account. The XRPL has roughly 785,000 of these.
By fetching all trustlines and filtering by issuer and currency, we can quickly extract a list of all IOUs currently issued on the XRPL: ~6,700 issued tokens, issuing tokens with ~1,100 different currency codes (remember that several entities can issue, e.g., a USD token).
So how do we determine if the “LOL” token represents real LOL value (?). There is no way to be certain, without knowing, and trusting the issuer. But we can define some parameters to narrow it down:
1: How many accounts are trusting the issued token?
Is just having more than one trustline the margin? Then the number already shrinks from ~6,700 to ~1,900 issued tokens. In this article, we want to focus on tokens that are broadly trusted; hence we can presume represents a value. We set the margin to having more than 50 trustlines, which leaves us with a list of 190 issued tokens and 84 currency codes.
The list went from ~6,700 to 190.
2: Manual filtering
By gathering intelligence, we know of some tokens that are issued either as fun or part of actual scams.
The list went from 190 to 134.
3 …: Additional parameters
To keep narrowing down the list to most plausible IOUs, we could look at, e.g., how many payments have been made with the token, the market depth, trading prices compared to average market trading prices, the connectedness of accounts with trustlines and much more.
Value represented on the XRPL
Given the list of 134 semi-verified IOUs, we can generate an overview of what kind of values are represented on the XRPL (a select list):
BTC: 14 issuers, ~36,500 trustlines, ~2,400 BTC
ETH: 1 issuer, ~24,000 trustlines, ~20,500 ETH
USD: 10 issuers, ~18,500 trustlines, ~33,000,000 USD
EUR: 3 issuers, ~10,000 trustlines, ~1,600,000 EUR
Conclusion
There are thousands of IOUs on the XRPL. But likely only a small fraction is representing real value. Circling back to the beginning, December 12, 2019. If we omit IOUs not part of the roughly filtered list of 134 tokens, how many BTC payments were actually sent? Four payments, 0.245 BTC in total.
Cover photo by Micheile Henderson @micheile010 // Visual Stories [nl] on Unsplash












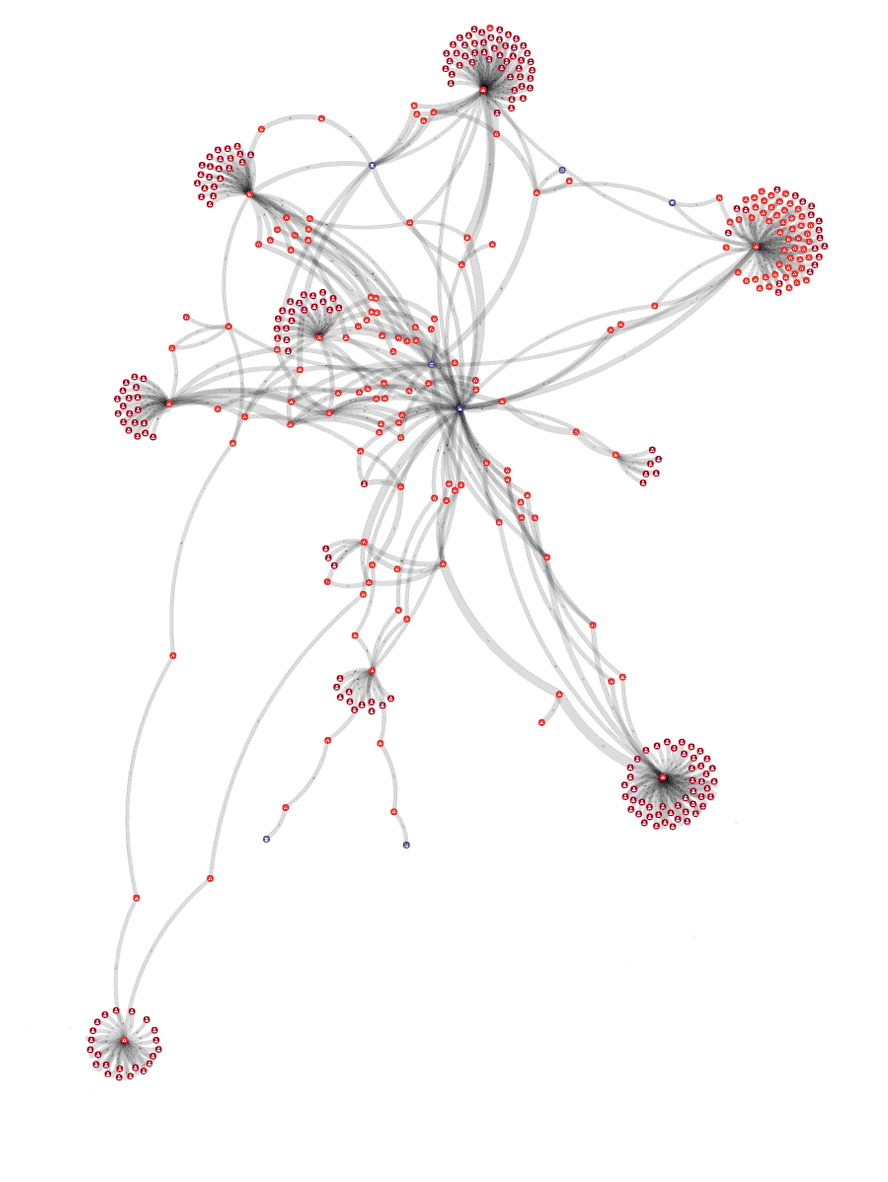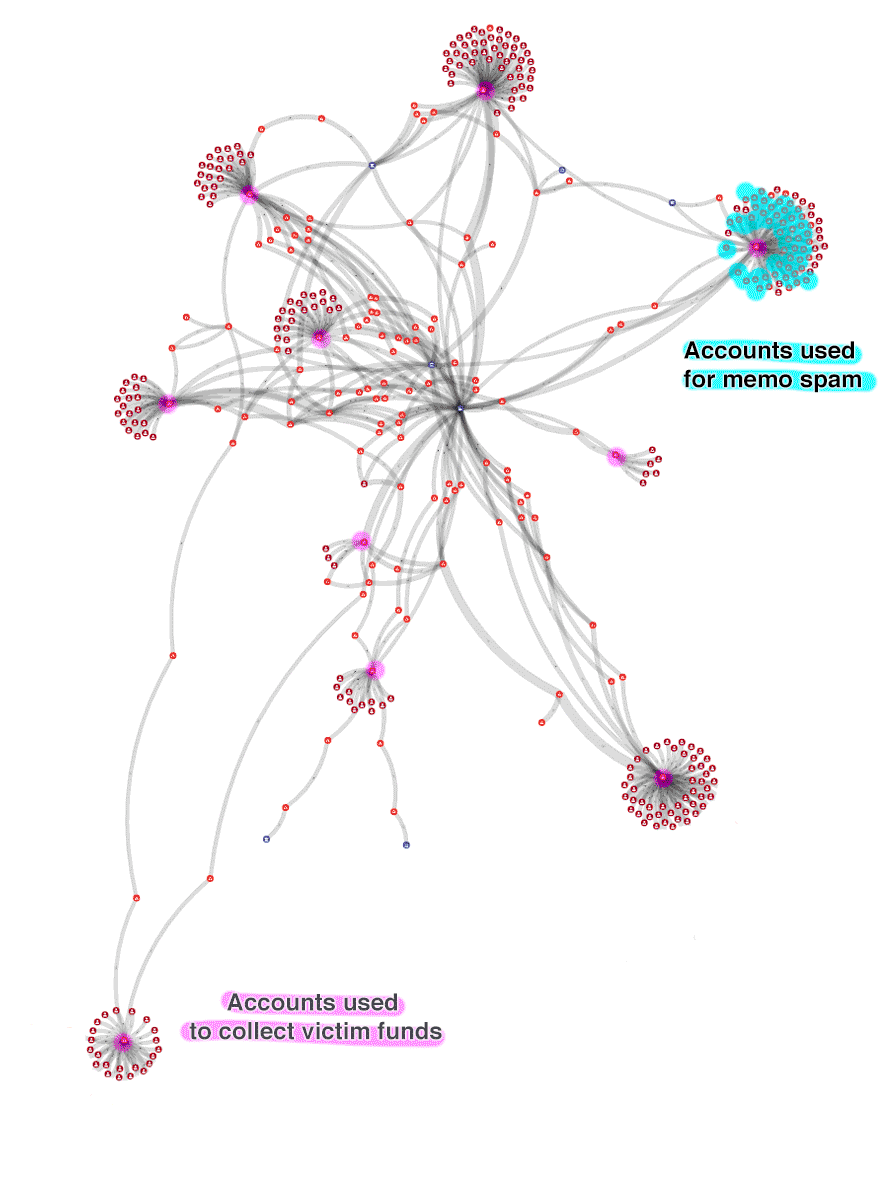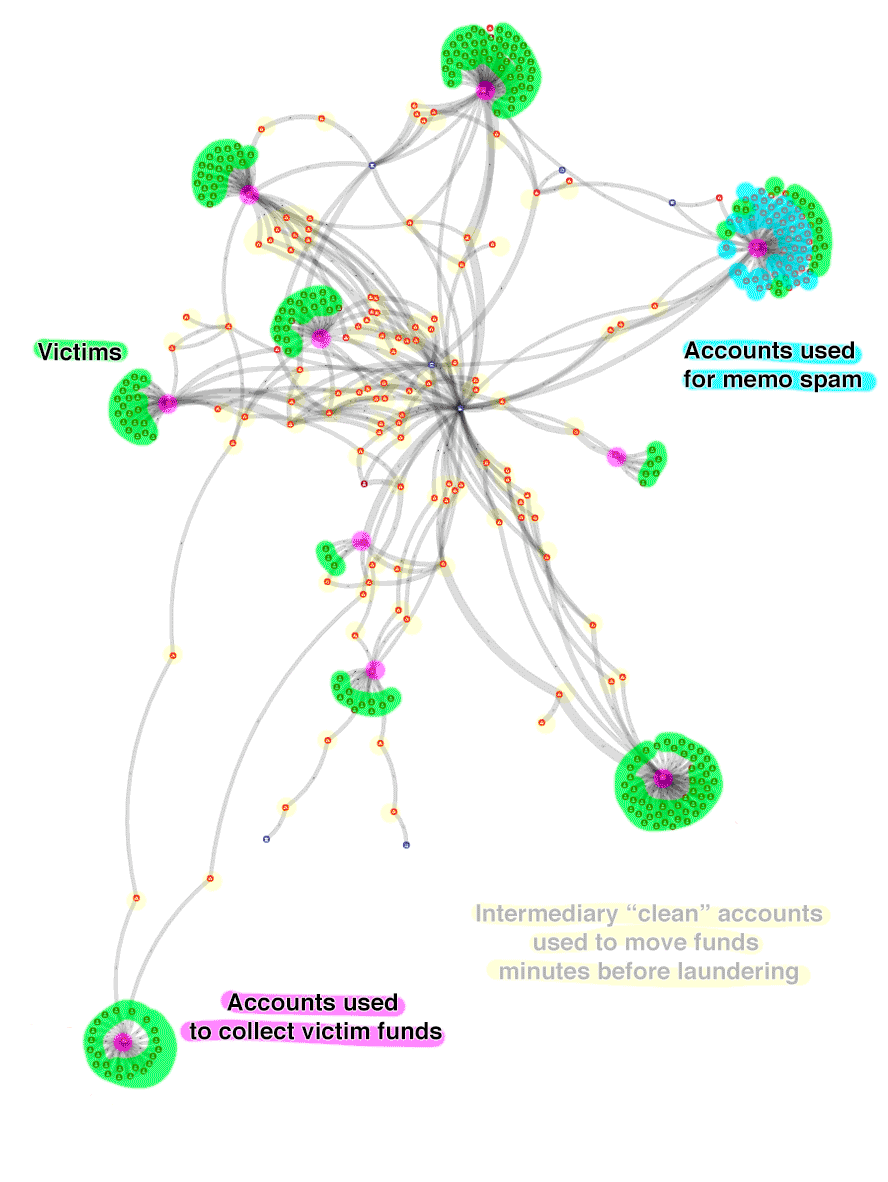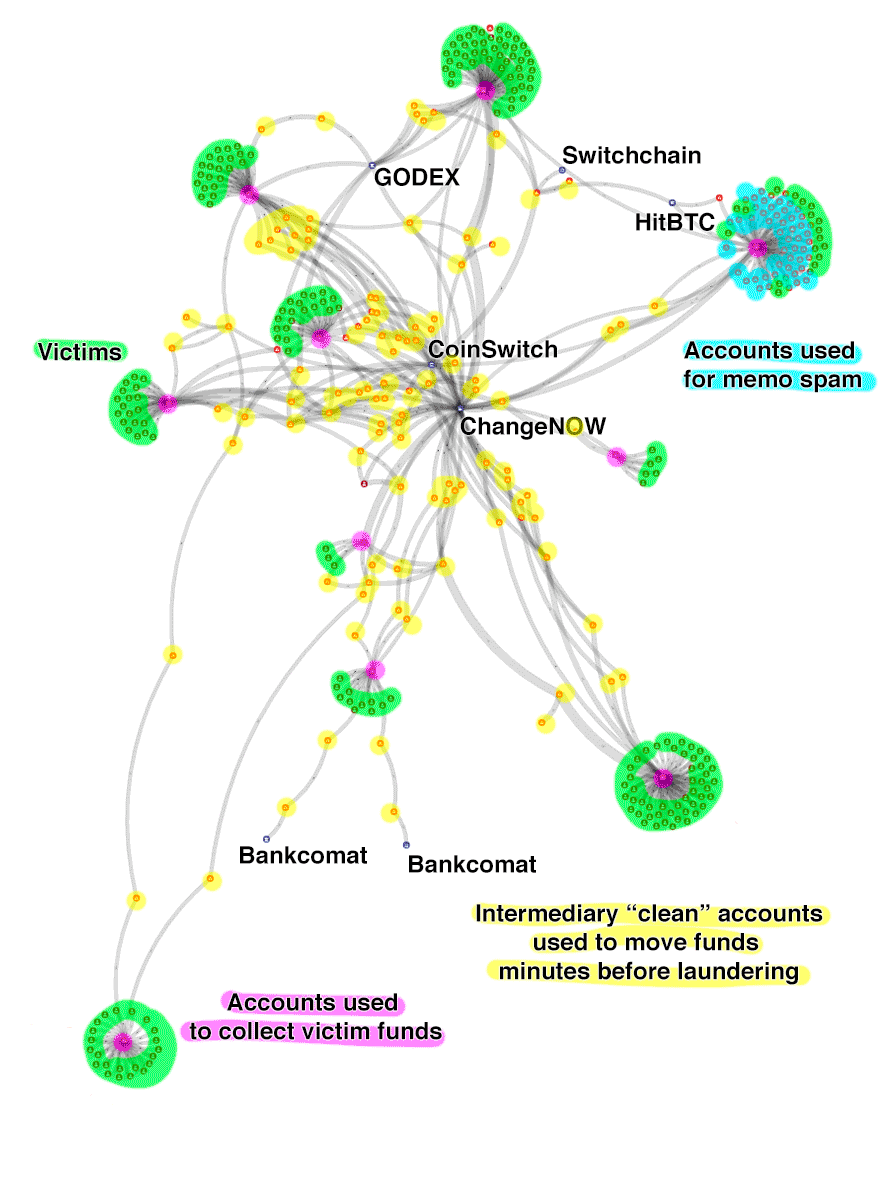







 The xrplorer data model
The xrplorer data model
