The homoglyph heist

On January 17, 2020, the first micropayments went across the ledger with memo messages like “Starting February 1st, 2020, Ripple is releasing 3 Billion XRP to incentivise network users. Get 25% more XRP added to your account balance in just minutes.” with a link to a website, appearing to be Ripple's Insights blog with a message about a grand giveaway.
With a well-crafted website, replicating websites well-known to most XRP investors, a well-written message, and domains that seemingly look right, the scam did succeed and the spam messages on payment memos continued for more than a month to lure users to new websites.
The warning signs
1. The domains are not the official domains, but homoglyph domains. A hòmoglyph ís a character that cân bë substituted for another, making it more difficult to quickly spot: ripple.com <> rípple.com.

2. If it sounds too good to be true, it probably is.
3.If you have to send money to participate, or even worse, send your account information and secret keys, don't do it.

Still, in a moment of weakness, people fall for the trap, and moments later, life savings are gone.
Cryptocurrencies: money or gambling?
That giveaway scams work, is not solely based on catching weak moments: it is also because of the unhealthy environment around cryptocurrencies; Instead of treating digital assets like money, it is promoted in line with gambling with legitimate giveaways, airdrops, and trading competitions.




With seasoned investors and traders used to navigate between the billboard signs of fake promises, for new traders and investors, it's a like a first casino visit – and with many fake giveaways looking more professional than many legitimate ones, it is a jungle to navigate.
The heist continues
All good movies get a sequel so, after roughly one month of memo spamming, it was time for a new wave of attacks in May 2020. This time, not with payment memos, but with e-mails targeted users likely interested in cryptocurrencies and XRP.
These e-mails have continued in waves from May and are still ongoing.
The loot
The entire heist operation is an elaborate setup with messages sent to XRP accounts based on their holdings, homoglyph domains, fake but trustworthy marketing material, tools to collect secret keys that also checks balance on the XRPL and much more. But looking on the ledger activity, we can also see the way of which they operate when laundering the money.
The account types:
Victims: Accounts belonging to users who have entered their account information on the phishing websites
Theft pool accounts: Accounts used to empty victim accounts in batches
Intermediary accounts: Accounts created by the thieves (typically in 2 degrees), just before sending money to a swap service, likely to avoid blacklists.
Memo spam accounts: Accounts created to send the memo spam messages
Exchanges: the exchanges receiving and laundering the stolen funds
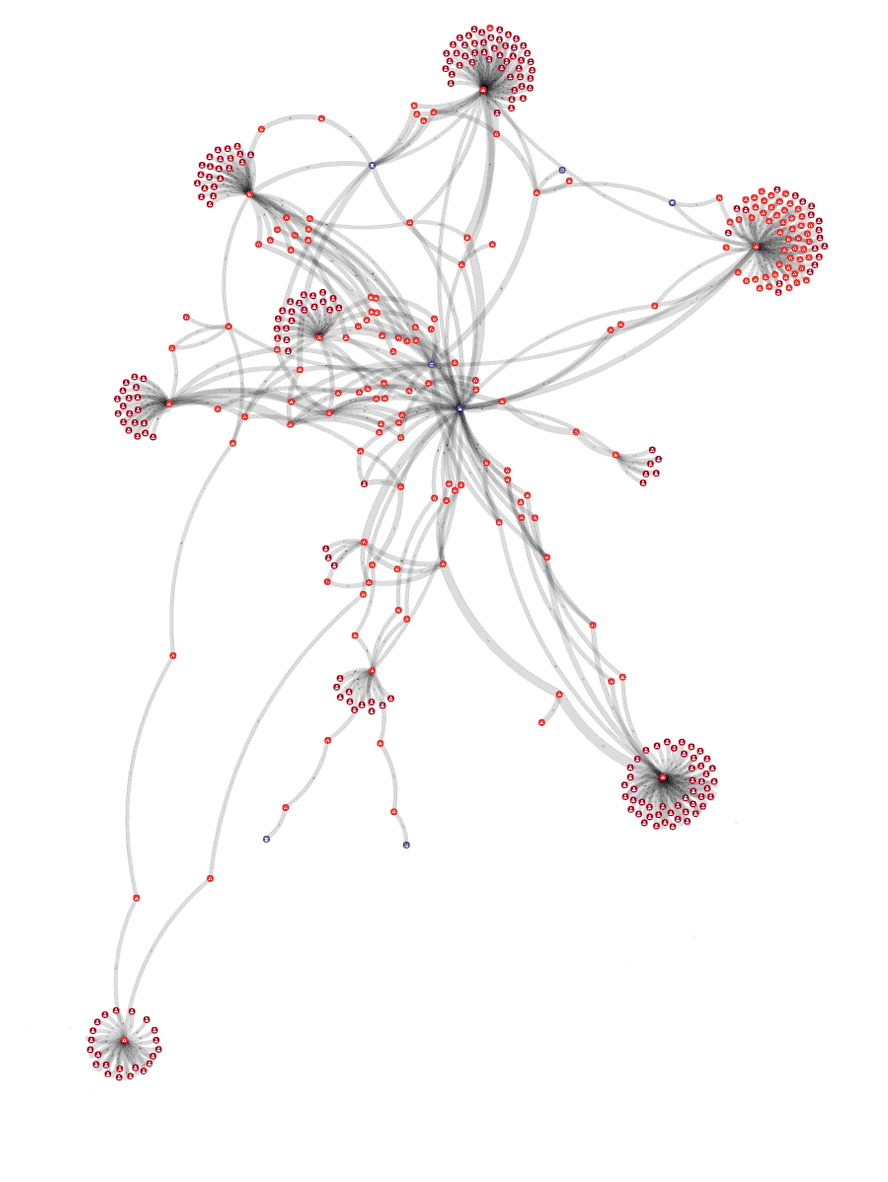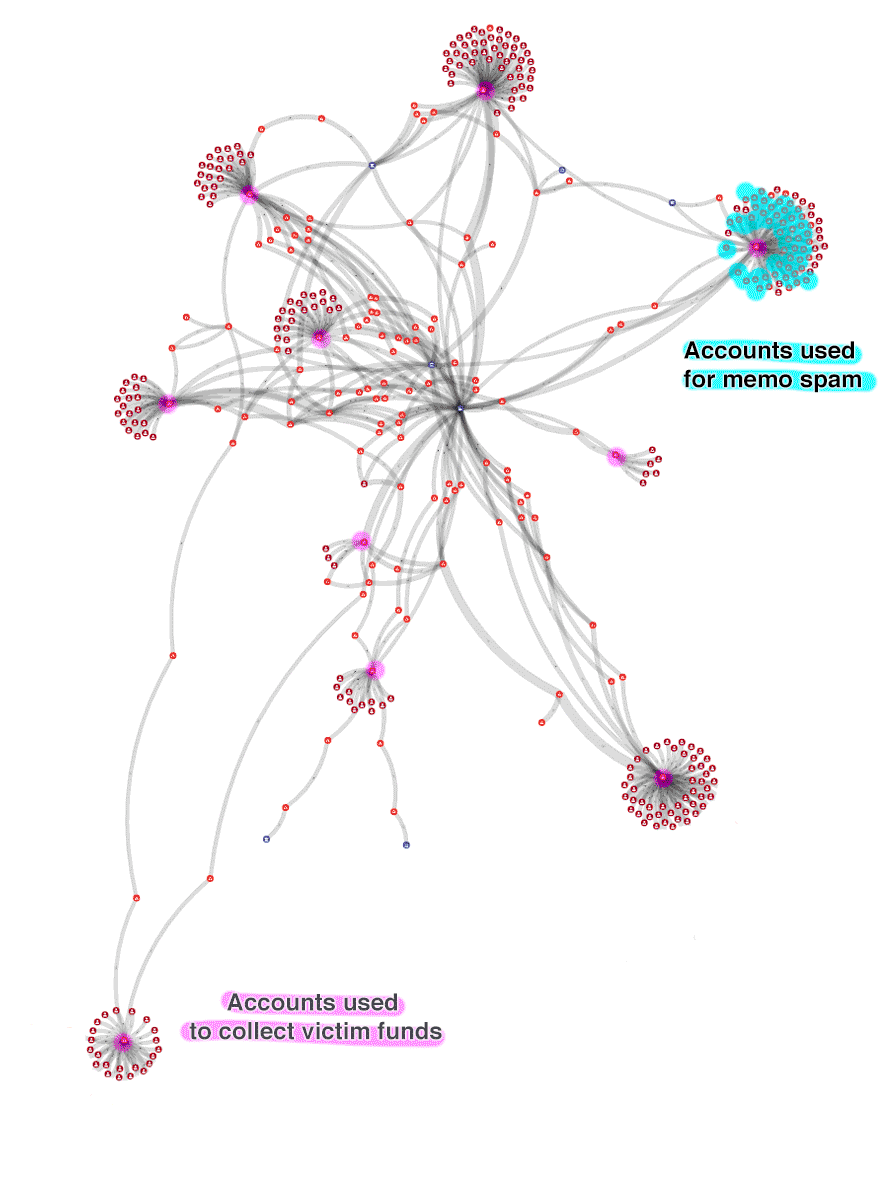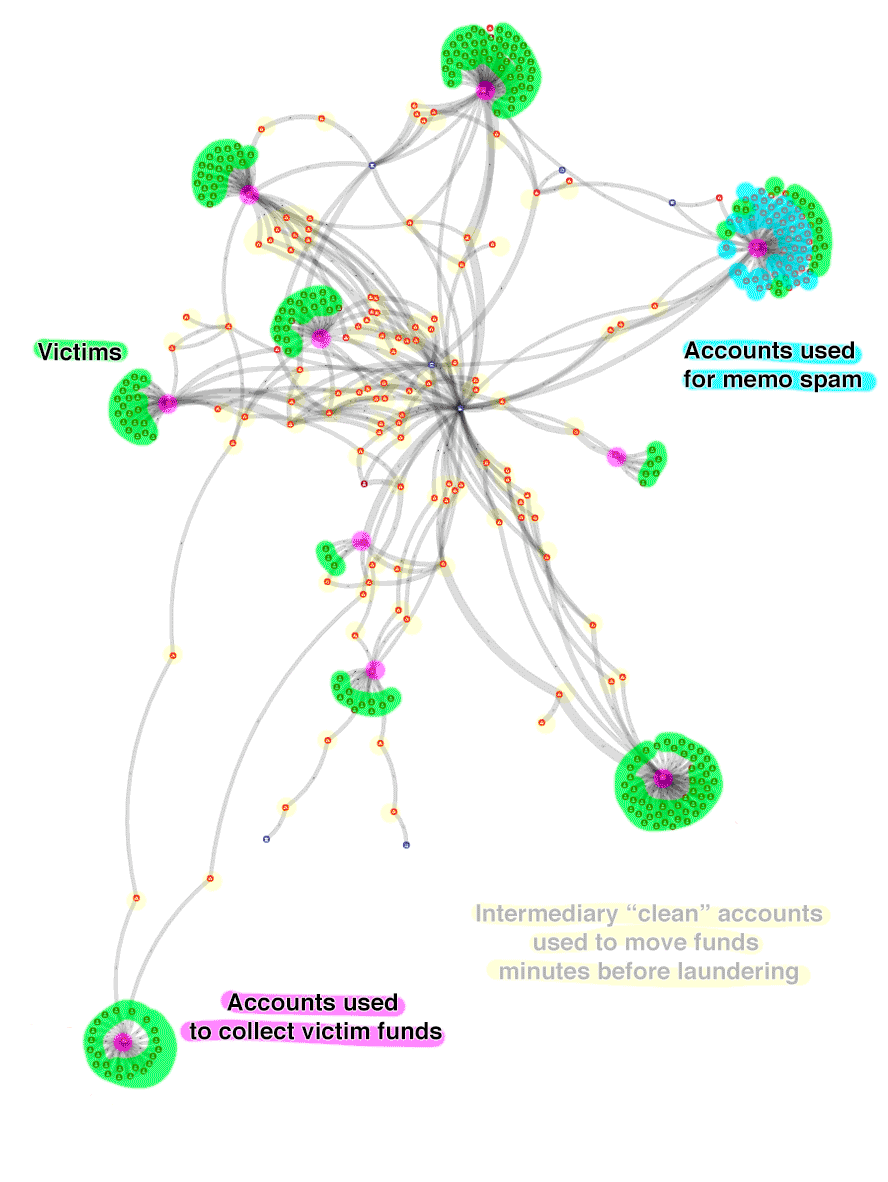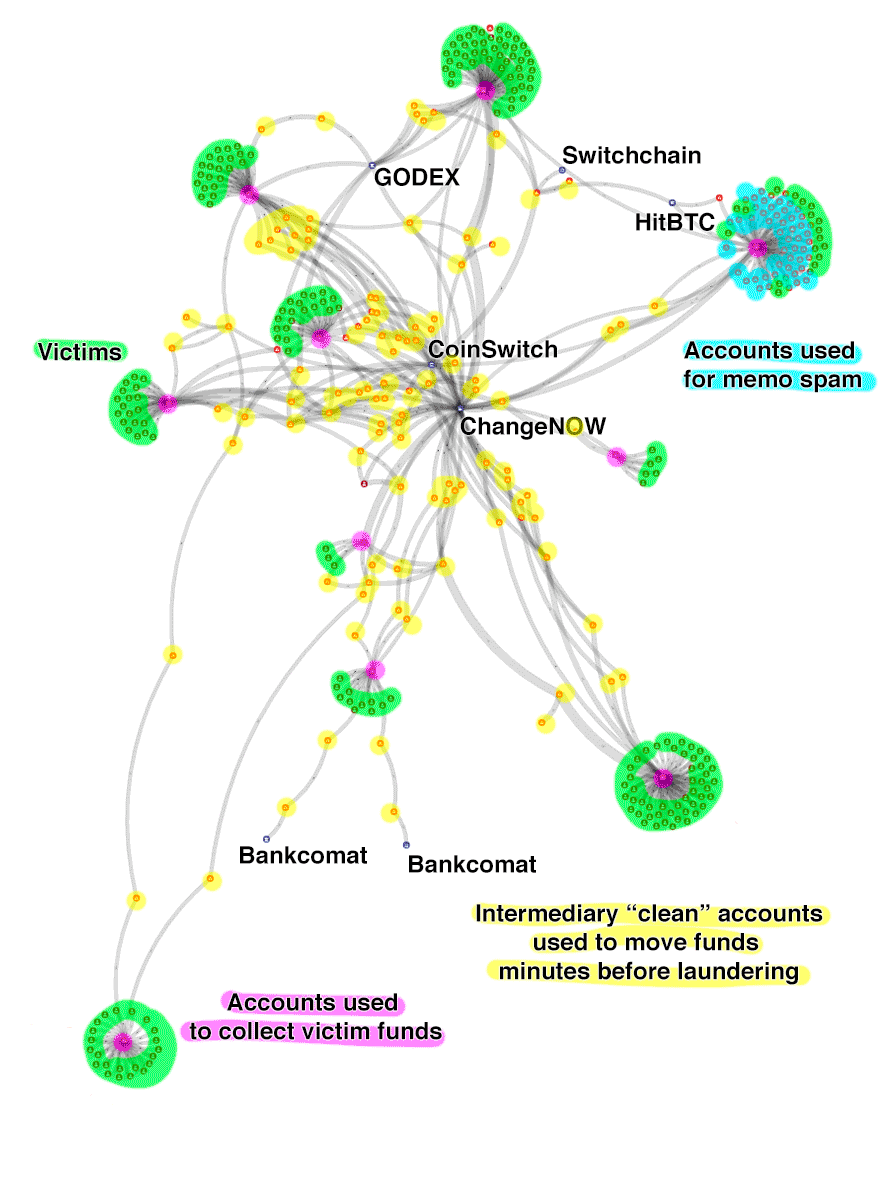
The graph is constantly changing as new victims appear and more money is laundered, but the current state (June 15) is more than 2,100,000 XRP stolen and 1,980,000 XRP laundered, mainly through to swap services: ChangeNOW and CoinSwitch.

Are you a victim?
The XRP ledger, like most other blockchains, is decentralised and no-one have the power to freeze or retrieve funds. So, if you have lost money, you need to file a police report with your local police.
Help us
We have monitored the activity since January, and receive push notifications every time new victims are made, or funds are laundered. By using our APIs, exchanges, swap services and other entities can help prevent XRP/IOU money laundering in real-time. You can help us by spreading the word to the services you use: https://xrplorer.com/forensics/advisorylist
The data in this article was generated with our XRP compliance toolbox: a collection of tools making it easy to extrapolate clusters and “follow the money”. Contact us for more information.
Photo by Luis Villasmil on Unsplash