Week 11 – Network Security: Class notes + Homework
#UofTBootcamp #netsec #cyberkillchain #c2 #homework #classwork
Follow-up Questions
11.1 Notes
– how does firewall affect zoom/signal?
– review TCP flags
– meaning of “stateness” as agnostic of network connection?
– ACTIVITY: blocking all ICMP pings – i thought this was not a good practice
Homework
Layered Security: multiple products to address a single aspect of security
- gateway (hardware) and firewall (hard and soft) to restrict access
- subset of defense in depth
- evaluated in three areas: administrative, physical, technical
- admin: policies and procedures, i.e. role-based access control (RBAC) or employee training against phishing scams
- physical: locking server rooms
Defense in Depth: Redundancy approach
- strategy leveraging multiple security measures so if one line of defense is compromised, additional layers are backup
- buys time to launch countermeasures if infiltrated
- addresses hardware, software, people re: negligence, human error
- includes anti-virus, firewalls, secure gateways, VPNs, machine learning to detect anomalies in behaviour of employees and endpoints
common issues organizations have to deal with when implementing a cybersecurity strategy:
- anti-malware software not updated or is not installed on all devices.
- Employees have not been trained and are falling victim to phishing schemes.
- Software patches are not being updated or are ignored.
- Security policies are not enforced or even known by employees.
- Missing or poorly implemented encryption.
- Remote employees are connecting to unsecured networks, such as the public internet.
- Physical security flaws, such as unsecured server rooms.
- Business partners, such as cloud service providers, are not fully secure.
Elements of Defense in Depth System:
1. Physical Controls: key cards to enter a building or scanners to read fingerprints 2. Net Sec controls: software authenticating employee to enter network/use device/application 3. Admin controls: authorizes employees, once authenticated, to access only certain applications or parts of the network 4. Antivirus: stops malicious software from entering network/spreading 5. Behavioural Analysis: algorithmns/ML can detect anomalies in the behaviour of employees and in the application and devices themselves
Core layers of defense in depth strategy should include:
- Strong, complex passwords
- Antivirus software
- Secure gateway
- Firewall
- Patch management
- Backup and recovery
least privilege
As companies grow and the number of devices, applications, and services used across the organization increases, these serve as important security layers in a defense-in-depth strategy:
Two-factor authentication (2FA) or multi-factor authentication (MFA)
Intrusion detection and prevention systems
Endpoint detection and response (EDR)
Network segmentation
Encryption
Data loss prevention
VPNs
Intrusion Detection and Attack indicators
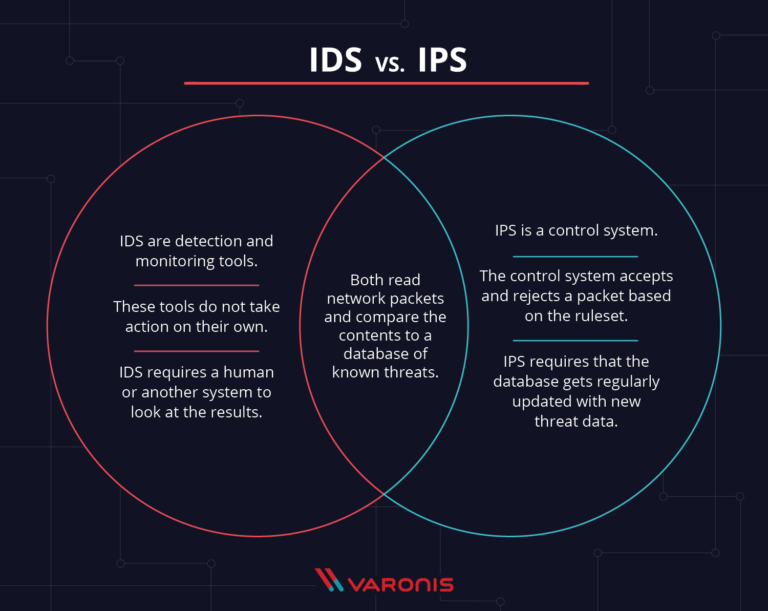
1. What's the difference between an IDS and an IPS?
IDS (Intrusion Detection System) is a detection and monitoring tool that doe snot take action on its own so a human (or another system) has to read and interpret the results. IPS (Intrusion Prevention System) is a control system that accepts or rejects a packet based on the rulelist — this means that unlike IDS, the IPS can take action against potential attacks.
Another difference is that IPS sits on the network in the same area as a firewall might (between the outside and internal network) so traffic has to flow through the IPS. An IDS only monitors the traffic, it is not in the line of traffic.
The last difference is that while both are known for generaeting false positives, in the event of an IDS, the false positive will only create alerts whereas for the IPS, this coudl cause the loss of important data or functions (again because it sits on the network).
2. What's the difference between an Indicator of Attack and an Indicator of Compromise?
An Indicator of Attack (IOA) focuses on detecting the intent of what an attacker is trying to accomplish regardless of the malware or exploit being used and is typically an alert before a network or application is exploited. On the other hand, an Indicator of Compromise (IOC) is regarded as the evidence that indicates a network security breach. It is usually gathered after a suspicious incident, on a scheduled basis or after an unusual discovery.
The Cyber Kill Chain
Name each of the seven stages for the Cyber Kill chain and provide a brief example of each.
1. Stage 1: Reconnaisance – Attackers pick a target and perform analysis, collect information (such as email addresses, conference information, technology stack, etc) and evaluate their target's weaknesses.
Example: Trying to discover what firewalls or intrusion prevention systems are in place for a targeted network. Using tools such as nmap, stan, or Strobe to search for vulnerabilities.
2. Stage 2: Weaponization – Attackers determine how best to get inside the network by exploiting the discovered vulnerabilities.
Example: Using a malware tailored to exploit the specific techhology that they discovered in the Reconnaisance stagethat the target network uses. Using a Zero-day vulnerability they have discovered.
3. Stage 3: Delivery – The chosen attack method is delivered to the target encironment.
Example: An infected USB drive is dropped off at the target office, a malicious attachment is sent via a phishing email, etc.
4. Stage 4: Exploitation– The attackers leverage the vulnerabilities and execute the malicious code on the target network.
__Example: __Triggering a Buffer overflow/underflow on a vulnerable database.
5. Stage 5: Installation – The malware weapon is installed, giving the attaker's an access point to the target environment, ideally one that they can return to effortlessly.
Example: A DLL Hijacking attack that exploits the way some Windows applicatons search and load Dynamic Link Libraries (DLL) by copying the name of a legitimate DLL and placing the malicious DLL in a position that the application will search first so that the malicious DLL will load instead. The malicious DLL could be written to launch the malware and then the legitimate DLL can be loaded to avoid suspicion, creating a persistent point of entry for the attacker.
6. Stage 6: Command and Control (C2) – The attackers have uninterrupted remote access to the target environment and can manipulate it to their choosing.
__Example: __
7. Stage 7: Actions on Objective – The original goal(s) of the attack can be executed.
Week 11.1 Notes: Intro Netsec + Firewalls
Defense in Depth: Perimeter || Network || Host || Application || Data
Net Sec Definition from SANS:
- physical and software preventative measures to protect underlying network infrastructure from unauthorized access, misuse, malfunction, modification, destruction, or improper disclosure
- goal is to create a secure platform for computers, user, programs to perform permitted critical functions within secure environment
Firewall: between application servers and routers to provide access control
- control access to single host or network
- first layer of defense on perimeter of the network's edge
- can slow connections, affect lack of connection, break networked apps like zoom, messager
- filter incoming/outgoing packets
- access policies / rules
Firewall Steps:
(1) Intercept traffic before it reaches target host or router (2) Inspect source and destination address, ports, TCP flags, and other features of incoming packets (3) Allow/deny packets
Firewall Types + OSI
MAC: useless comparison to approval list, can be spoofed easily
STATELESS Packet Filtering : create checkpoints within a router and examine packets as they progress through an interface; if not pass inspection, drop – stateless = does not care about network connection – layer 3-4 – statically evaluate contents of packets and do not keep track of the state of a network connection – use rules based on individual packets such as: source/destination IP, source/destination port info, IP protocols, Ingress and egress interface – vulnerable to spoofing, no custom rules
STATELESS Packet Filtering : still L3-4 but is stateful so it can determine whether a packet is NEW, ESTABLISHED, or rogue bc it understands context of entire data stream. – statefull firewalls do not look at individual packets but connection as a whole – inspect packets' conversation and routing tables, use a combination of TCP handshake verification and packet inspection tech – cannot determine what traffic is doing, only identify that a connection is using x protocol, not what the payload is
Circuit-level gateways: SESSION LAYER – verify the TCP handshake by looking at the HEADER of a packet only – NOT PAYLOAD – TCP handshake checks verify: unique session identifier, state of connection (established vs closed), sequencing info – ensures that session packets are from legit sources – fast/easy but does not check contents of packets – if packet contains malware but has correct TCP, data is allowed to pass
Application gateways: Proxy firewalls L3-7, STATEFUL – inspect actual contents of packet, including authentication and encryption – use deep packet inspection and stateful inspection to determine if incoming traffic is safe or harmful – intercept all traffic without data source knowing – connection is established to proxy firewall which inspects traffic and passes/drops – more secure, provides log/file audit – resource intensive, requires hardware, bypassed with encryption
UFW: Uncomplicated Firewall: provides stateless and stateful packet filtering
- works on all kinds of network address and port translation, i.e. NAT, NAP (Network Addressing Protection)
- manage multiple devices over
CLIUFW features: - host-based
- multi-level logs, great insight into attacks
- remote management – security concern?
- rules for allow/deny regarding: source/destination IP addresses, port numbers, packet types — all without opening packet
- TCP handshake, packet inspection
- rate-limited connections to protect from brute force DISADVANTAGE: all firewall services must be stopped/restarted for changes, interrupting service
firewalld: dynamically managed firewall w/o disruption using zones to divide network interfaces into groups of shared trust level
Zones: each zone has rules/configs that can runtime (valid until next reboot or service reload, used for testing) or permanent Services: designate which service you want ot allow, it will automatically open those ports
11.1 Activities
Activity UFW (Uncomplicated Firewall)
– need to have ports 110, 143, 587, 80, 443 to be open at all times as part of its daily operations.
-