The Power To Serve: Custom Kernel Goodness on FreeBSD
For those who are unfamiliar with FreeBSD, it's a unique system that feels distinctly like the UNIX of old- because it is. Last post, we installed FreeBSD, got connected and installed some software. You might have even gotten a desktop working on your own, because it feels so much like Linux. However, the stock install is a bit RAM hungry and we aim to improve that.
Kernel? What's a Kernel?
Like Linux, FreeBSD (and Windows and MacOS) all have an underlying Kernel. This is basically a loose term that describes all the underlying components that the user doesn't see day-to-day when utilizing an Operating System, such as firmware and drivers being loaded, support for multithreading, filesystem support, and so on. Because BSD has so much support for strange devices- like VAX machines of old- it's expected of users who wish to optimize their systems to purge unneeded support from their system.
Getting Started
Of course, you'll need a FreeBSD installation with the source code to follow along... :) However, we'll need some more details about our target system that we'll be rolling a custom Kernel for. So let's whip out a notepad or text editor and our trusty command line. The trusty dmesg command will come in handy, but it produces way too much output, so we can filter that with grep by doing something like dmesg | grep <search term>.
The laptop I did this on was an unmodded Thinkpad T460. I knew that it came with Intel Wireless, an Intel CPU, an SSD, and Intel Integrated Graphics, for starters. But what model?
So I ran dmesg | grep Wireless and got the following output:
iwm0: <Intel(R) Dual Band Wireless AC 8260> mem 0xredacted at device redacted
Note that I have censored the last bit of output for privacy, but it contains memory address and what part of the PCI bus it's connected to.
I took note of this and did similar commands to gather info on my hardware.
Backing Up
Since we're replacing our kernel, we want a backup of the last known good one. In FreeBSD, the current running kernel is located at /boot/kernel. So let's make a copy in /boot, so we can continue to use it if things go south!
Running cp -a /boot/kernel /boot/kernel.good will do the trick for this.
Config Time!
Now we get to prep our Kernel config file. To do so, cd /sys will take you to the /sys directory, where you'll see a few architecture names as directories: x86, x64, arm, etc. My ThinkPad T460 is a 64 bit x64 processor, so I ran cd x64.
Now, there's a folder in this directory called conf. That's where the config files are located- so cd conf and then run ls to view the available config files to start from.
Instead of altering the config files directly, it may be wise to make a copy of one. I picked the GENERIC config file and copied it into one in the same directory, naming it T460 (no file extensions!!!)
With this done, open the freshly copied config file in the text editor of your choice. In this config file, there's lots of comments, specifying what each option will compile into the kernel. Removing the line will remove the feature from your compiled kernel. Since my ThinkPad doesn't have a floppy disk or RAID controller that's easy enough to remove those. I know that I have Intel Wired and Wireless connections, so I can remove all support for other network cards if I so choose.
ATCHUNG! Read what each option enables support for before deleting the line, and make sure you're not removing things that are critical to the function of your hardware!
Once satisfied, save the new config and quit.
Updating the Source
First things first, we need to install and set up subversion (SVN) on FreeBSD to get the latest copy of the FreeBSD source tree. In order to install SVN and get it ready to rock, we just need to run pkg install ca_root_nss subversion.
Now with SVN installed, let's fetch a copy of the latest source tree. If you already have the source code installed, run svn update /usr/src/. If not, we need to fetch a copy by running svn checkout https://svn.freebsd.org/base/releng/12.1 /usr/src/ (replace the 12.1 with the version number of FreeBSD you installed.)
Awesome! We're ready to compile the kernel!
Compiling the Kernel
With your freshly updated copy of the FreeBSD source code, cd /usr/src to get into the source code. Since our config file is prepped, all you have to run is make KERNCONF=CONFIG buildkernel– swap out the word CONFIG for your kernel config name. This will take a bit to compile, so grab a coffee or something while waiting. When it finishes, you run make KERNCONF=CONFIG installkernel, again swapping out the word CONFIG for your actual config filename. When finished, reboot your system and test it out!
BRO! MY KERNEL IS CRASHING!
In the bootloader, you can switch back to the old kernel to resolve the issues in your config and re-attempt compiling the kernel until satisfied.
What Are The Benefits of Doing This?
On my ThinkPad T460, the stock system used about 1.7 gb of RAM. After the custom kernel, it's now using 800 Mb of RAM- to lower the usage even further, some tunable “knobs” in /etc/rc.conf, /etc/loader.conf and /etc/sysctl.conf prove useful as well.
Another interesting thing to note is that this Kernel config can be used to rebuild the ENTIRE SYSTEM as well, using the make KERNCONF=CONFIG buildworld and make KERNCONF=CONFIG installworld commands too.
Until next time!
 The FreeBSD Installer
The FreeBSD Installer In prompts like this one, you'll need to use the space bar to alter selections.
In prompts like this one, you'll need to use the space bar to alter selections.
 Assuming this signal repeats 1 milion times a second, we could say it operates at 1 MHz (1 Megahertz)
Assuming this signal repeats 1 milion times a second, we could say it operates at 1 MHz (1 Megahertz) Sine Waves have different degrees of phase, totalling to 360 like a circle. Above, the wave has been split into 90 degree chunks.
Sine Waves have different degrees of phase, totalling to 360 like a circle. Above, the wave has been split into 90 degree chunks.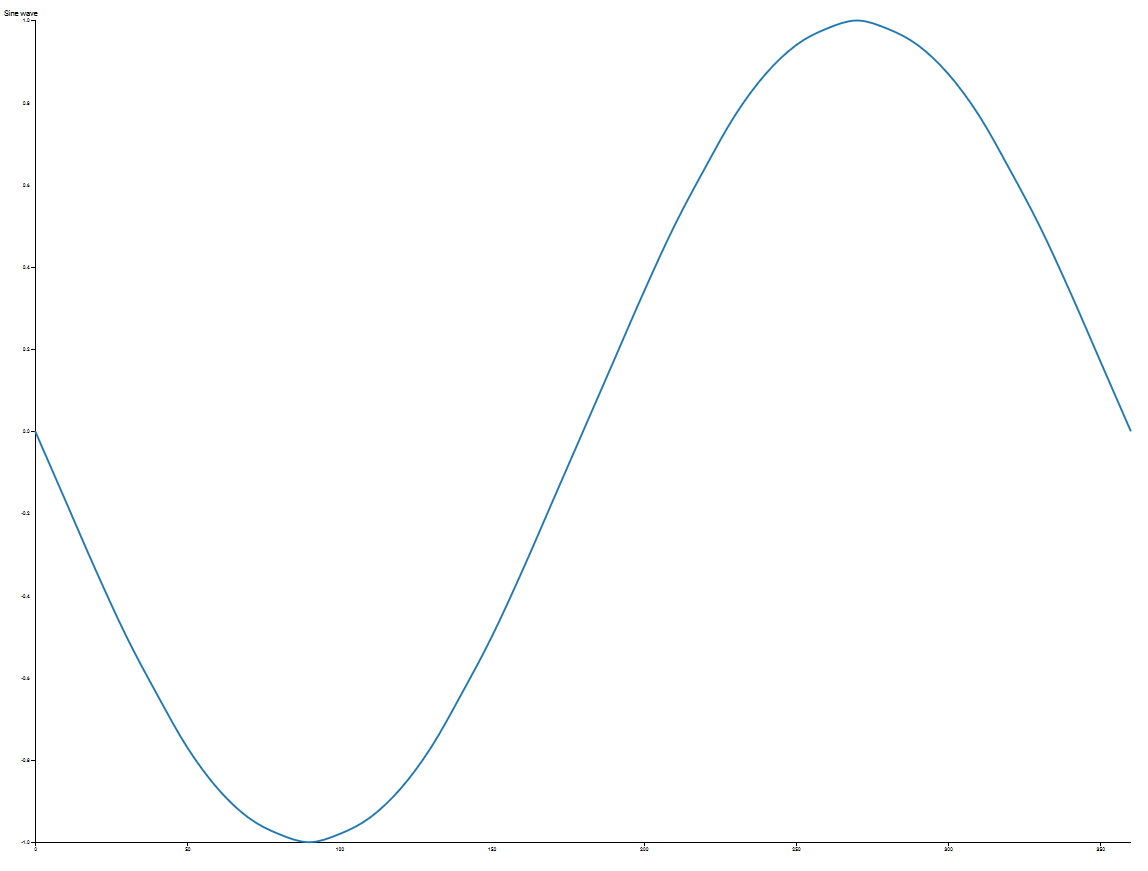
 Take this slowly! Don't destroy your mouse buttons!
Take this slowly! Don't destroy your mouse buttons!
 You will need your needlenose pliers and the file to obtain this shape.
You will need your needlenose pliers and the file to obtain this shape. The screws circled in red underneath the middle cover can be thrown away or reused, as reinstalling them will kill your classic keyboard. Otherwise, save the screws.
The screws circled in red underneath the middle cover can be thrown away or reused, as reinstalling them will kill your classic keyboard. Otherwise, save the screws.




